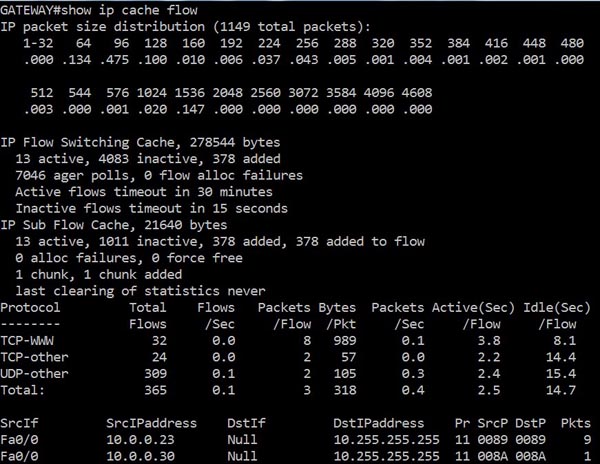
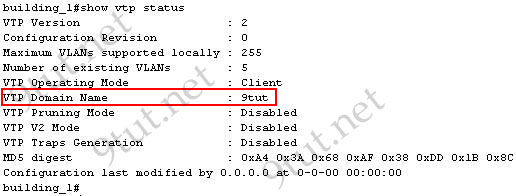
Once IOS has finished loading up, it will ask you to press Return to continue. While waiting for you to press return, it will display the status of every interface as shown below.
Press RETURN to get started!
*Mar 1 00:09:01.271: %LINK-5-CHANGED: Interface FastEthernet0/0, changed state to administratively down
*Mar 1 00:09:01.583: %LINK-5-CHANGED: Interface FastEthernet0/1, changed state to administratively down
*Mar 1 00:09:02.271: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to down
*Mar 1 00:09:02.583: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down
Once you press enter, you will arrive at the Router> prompt. If the router has a startup config with authentication configured, such as in the case of most brand new ISRs, you will be prompted for a username and/or password before you will arrive at the prompt. For new ISRs cisco is the username and password. We will cover authentication later in the chapter. For now consider the prompt that you will see. The text before the greater-than sign (>) is the hostname of the device. By default Router or Switch is the default name depending on the device.
IOS modes
The CLI of the IOS is divided into different modes or levels. Each mode serves a different purpose and has different sets of commands. It is important to be familiar with different modes that you will encounter in this book. Covering all the modes is out of the scope of CCNA.
The character after the hostname of the device tells you which mode you are in. When you first start a router and press enter, you are at theRouter> prompt. The greater-than sign (>) tells you that you are in the user exec mode or level 1. This mode is mostly used to view statistics. You cannot view or edit configuration of the device from this mode. This mode also serves as the stepping-stone to the next mode, the privileged exec mode or level 15. At this level the prompt changes to the dollar sign (#). To go to the privileged exec mode from the user exec mode, type enable command on the prompt and press enter as shown below. Notice the change in prompt after the command is entered.
Congratulations! You just entered your first command on an IOS device.
To go back to the user exec mode, you can use the disable command as shown below:
To close the CLI session, use the logout command in any mode.
At the privileged exec mode you can view the configuration and statistics related to every component and process of the device but cannot make changes to the configuration. To be able to make changes to the configuration of the device, you will need to go to the global configuration mode using the configure terminal command in the privileged exec mode as shown below. Notice that the prompt changes toRouter(config)# after you enter the command. (config)# tells you that you are in the global configuration mode.
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#
In this mode, you can make changes to the configuration of the device. You must remember three things about the global configuration mode:
- All changes affect the running config. These changes are not persistent after a reboot unless running config is saved to the startup config.
- All changes have an immediate effect on the device.
- The global configuration mode has sub-modes. While some changes can be made in the global configuration mode, changes to specific components, such as interfaces, must be done in dedicated sub-modes.
From the global configuration mode you can go to different sub modes to configure specific components. While most of the sub modes are beyond the scope of CCNA, a few of the modes that you will come across in the book are discussed in Table 3-4.
Table 3-4 IOS Sub-modes
| Sub-mode name | Purpose | Sub-mode prompt | Command to enter sub-mode |
| Interface Configuration | In this mode you can configure individual interfaces of the device. You can configure protocol, layer 3 addressing etc. in this mode. | Router(config-if)# | interface <interface-name>
Example:
Router(config)#interface fastEthernet 0/0
Router(config-if)#
|
| Line configuration | In this mode you can configure the console, telnet and auxillary lines, which are used for exec sessions. | Router(config-line)# | line {con | vty | aux}number
Example:
Router(config)#line console 0
Router(config-line)#
|
| Routing Configuration | In this mode you can configure the routing protocols. | Router(config-router)# | router protocol [number]
Example:
Router(config)#router rip
Router(config-router)#
|
IOS Editing and Help Features
While configuring a device running IOS, using the CLI is mostly about remembering the different commands and options. Cisco makes it easier to do this by providing various editing and help features. The help feature is a lifesaver. You can use a question mark (?) at any place to see a list of available commands or options, as shown below.
Router#configure ?
confirm Confirm replacement of running-config with a new config
file
memory Configure from NV memory
network Configure from a TFTP network host
overwrite-network Overwrite NV memory from TFTP network host
replace Replace the running-config with a new config file
terminal Configure from the terminal
<cr>
In the above output when a question mark (?) is entered after the configure command, a list of available options is displayed. Notice thatterminal is one of the options. Another example is given below.
Router#?
Exec commands:
access-enable Create a temporary Access-List entry
access-profile Apply user-profile to interface
access-template Create a temporary Access-List entry
alps ALPS exec commands
archive manage archive files
audio-prompt load ivr prompt
auto Exec level Automation
beep Blocks Extensible Exchange Protocol commands
bfe For manual emergency modes setting
call Voice call
ccm-manager Call Manager Application exec commands
cd Change current directory
clear Reset functions
clock Manage the system clock
cns CNS agents
configure Enter configuration mode
connect Open a terminal connection
copy Copy from one file to another
credential load the credential info from file system
crypto Encryption related commands.
ct-isdn Run an ISDN component test command
–More–
In the above output, the numbers of options are more than the available screen size, hence the output pauses and you see the –More– text. At this point you can press space to see the rest of the output or press q to quit back to the prompt. A final example of the help feature is given below.
Router(config)#i?
identity interface ip ipc
iphc-profile ipv6 ipx irec-agent
isis iua ivr ixi
In the above output notice that a question mark was entered after a single character. This causes IOS to display a list of options starting with that character. You can enter a question mark after multiple characters to see a list of options starting with those characters. For example, type in? at the above prompt will show a list consisting of interface option only. This brings up an interesting feature of the CLI. If you type a few characters which are unique to a command and press the tab key, the IOS will complete the command for you. In fact if you type the first few unique characters of the command, you need not press tab or complete the command. IOS will understand which command you want. For example if you type int and press tab then IOS will complete the command. Another example is shown below.
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#
Notice that the configure terminal command is executed at conf t. The IOS sees that the only command which starts with conf is configure,while terminal is the only option which starts with t.
Apart from these help features, the IOS provides some meaningful messages when you enter an incomplete or wrong command. Take a look at few of these messages shown below.
Router#confguire terminal
^
% Invalid input detected at ‘^’ marker.
The above message tells that there is an error in the command marked by the caret sign (^). Because of the sign, it is easy to see that there is a typing mistake in the command.
Router(config)#interface
% Incomplete command.
The above message tells that you have entered and incomplete command. More options are needed with the command. In such a situation, you can use the question mark after the command to see available options.
Router(config)#s
% Ambiguous command: “s”
The above message shows that you have not typed enough unique characters. There are multiple commands that start with the characters that you have entered.
While using the CLI, these help features and messages are immensely useful, but you also need to know about a few key combinations that you can use while typing commands. Table 3-5 shows a list of these key combinations.
Table 3-5 IOS editing key combinations
| Key or Combination | Purpose |
| Left Arrow or Ctrl+b | Move cursor one character back |
| Right Arrow or Ctrl+f | Move cursor one character forward |
| Esc+b | Move cursor one word back |
| Esc+f | Move cursor one word forward |
| Ctrl+a | Move cursor to the start of line |
| Ctrl+e | Move cursor to end of line |
| Ctrl+d or Backspace | Delete one character before the cursor |
| Ctrl+w | Delete one word before the cursor |
| Ctrl+u | Deletes the entire line |
| Ctrl+z | Leave configuration mode and go back to privileged exec mode |
| Ctrl+p or Up arrow | Shows the previous command entered |
| Ctrl+n or Down arrow | Shows the next command entered after up arrow/Ctrl+p has been used. |
Another useful feature of the CLI is the show history command. This command lists the last 20 commands that you have entered in the session. An example is shown below:
Router#show history
enable
configure terminal
exit
show version
show run
show history
The number of commands that can be stored by the router in the history can be changed using the terminal history size command. You use the command to change the size of history from 0 to 256. An example is shown below:
Router#terminal history size ?
<0-256> Size of history buffer
Router#terminal history size 25
The configured size of the history can be confirmed by using the show terminal command as shown below:
myRouter#show terminal
Line 194, Location: “”, Type: “XTERM-COLOR”
Length: 45 lines, Width: 202 columns
Baud rate (TX/RX) is 9600/9600
Status: PSI Enabled, Ready, Active, No Exit Banner, Automore On
Capabilities: none
Modem state: Ready
Special Chars: Escape Hold Stop Start Disconnect Activation
^^x none – – none
Timeouts: Idle EXEC Idle Session Modem Answer Session Dispatch
00:10:00 never none not set
Idle Session Disconnect Warning
never
Login-sequence User Response
00:00:30
Autoselect Initial Wait
not set
Modem type is unknown.
Session limit is not set.
Time since activation: 00:00:31
Editing is enabled.
History is enabled, history size is 50.DNS resolution in show commands is enabled
Full user help is disabled
Allowed input transports are pad telnet rlogin lapb-ta mop v120 ssh.
Allowed output transports are pad telnet rlogin lapb-ta mop v120 ssh.
Preferred transport is telnet.
No output characters are padded
No special data dispatching characters
In the above output, you can see that history is enabled and the history size is 50.
The last feature of CLI that you need to know about before proceeding is the do command. As you already know, commands can only be entered in particular modes. For example, show terminal command can be executed only in the user privilege mode and not in the configuration mode. If you are in the configuration mode or one of the sub-configuration modes, you will need to exit out of that mode and get back to the user privilege mode to execute that command. This can be inconvenient at times when you want to quickly verify something while configuring the device. To get around the need to exit back to the user privilege mode, you can use the do command followed by any privilege exec mode command to execute it from any mode you are. For example, the do show terminal command at the configuration mode will execute the show terminal command as if you were in the privilege exec mode. The example below shows what happens when the command is executed with and without do:
Router(config)#show terminal ^
% Invalid input detected at ‘^’ marker.
Router(config)#do show terminalLine 194, Location: “”, Type: “XTERM-COLOR”
Length: 45 lines, Width: 202 columns
Baud rate (TX/RX) is 9600/9600
Status: PSI Enabled, Ready, Active, No Exit Banner, Automore On
Capabilities: none
Modem state: Ready
Special Chars: Escape Hold Stop Start Disconnect Activation
^^x none – – none
Timeouts: Idle EXEC Idle Session Modem Answer Session Dispatch
00:10:00 never none not set
Idle Session Disconnect Warning
never
Login-sequence User Response
00:00:30
Autoselect Initial Wait
not set
Modem type is unknown.
Session limit is not set.
Time since activation: 00:00:14
Editing is enabled.
History is enabled, history size is 20.
DNS resolution in show commands is enabled
Full user help is disabled
Allowed input transports are pad telnet rlogin lapb-ta mop v120 ssh.
Allowed output transports are pad telnet rlogin lapb-ta mop v120 ssh.
Preferred transport is telnet.
No output characters are padded
No special data dispatching characters
In the above output, notice that the first command generated an error. But when it was executed with a preceding do command, it was executed.